Want to learn cyber security?
CISO Tradecraft® delivers fun, expert-led cybersecurity podcasts across core CISO domains. From leadership and risk to cloud, AI, governance, and defense. Learn practical tradecraft for beginners and seasoned security leaders. Subscribe to our Newsletter for insights that matter. THANK YOU!
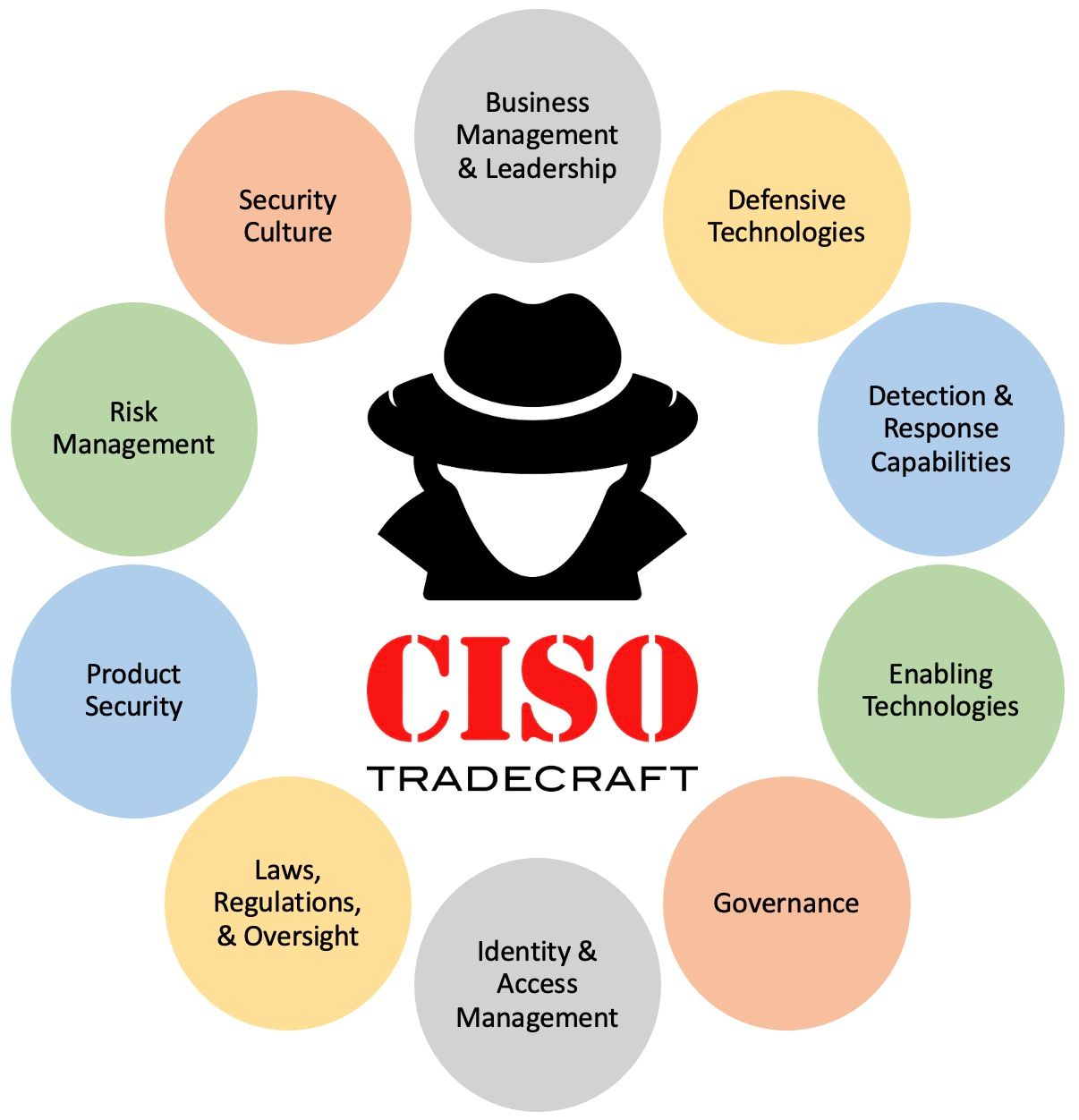
This topic is used to increase understanding about the position of a Chief Information Security Officer (CISO). It also provides tips to help cyber executives succeed such as Building a Cyber Strategy.
- What is a CISO
- 12 CISO Templates (with Ross Young)
- 3 Business Objectives & 5 CISO Archetypes (with Christian Hyatt)
- 7 Ways CISOs Setup for Success
- Board Decks (with Demetrios Lazarikos)
- Career Lessons from a CISO (with John Hellickson)
- CISO Knowledge Domains Part 1
- CISO Knowledge Domains Part 2
- How do CISOs spend their time?
- How to Win Your First CISO Role
- Lessons Learned as a CISO (with Gary Hayslip)
- Negotiating Your Best CISO Package (with Michael Piacente)
- Refreshing Your Cybersecurity Strategy
- The CISO Mindmap (with Rafeeq Rehman)
- 2024 CISO Mindmap (with Rafeeq Rehman)
- The 3 Keys to being a CISO (with Allan Alford)
- The 30 Year CISO Evolution
- The Professionalization of CISOs (with Steve Zalewski & Tyson Kopczynski)
- Updating the Executive Leadership Team on Cyber
- Updating the Mindmap (with Rafeeq Rehman)
- Your First 90 Days as a CISO (with Mark Egan)
Business Management & Leadership is an essential skill for executives to lead and influence others. These soft skills are critical to organizations where politics requires effective leaders to implement change via large collaboration efforts.
- 1% Better Leadership (with Andy Ellis)
- A Black Hat Chat with ThreatLocker CEO Danny Jenkins
- Accepted Cyber Security Strategy (with Branden Newman)
- Addressing the Top CEO Concerns
- Connecting the Dots (with Sean Heritage)
- Crisis Leadership (with G Mark Hardy's 9/11 Experience)
- Crucial Conversations
- Effective Meetings
- Emotional Intelligence
- Ensuring Profitable Growth
- Executive Competencies
- Executive Presence
- Framing Executive Discussions
- Gaining Trust (with Robin Dreeke)
- Grey is the New Black (with Ryan Gooler)
- How to Read Your Boss
- Leading with Style
- Master Storytelling for CISOs (with Neal Ford)
- Maximize the Outcomes Per Dollar in Cyber (with Ross Young)
- Maximize Your Cybersecurity Budgets (with Ross Young)
- New Kid in Town (with Rebecca Mossman)
- Partnership is Key
- Presentation Skills
- Principles of Persuasion
- Promotion through Politics
- Reality-Based Leadership (with Alex Dorr)
- Responsibility, Accountability, and Authority
- Show Me the Money (with Nick Vigier)
- Speak My Language (with Andrew Chrostowski)
- Team Building
- The Demise of the Cybersecurity Workforce
- The Great Resignation
- The Right Stuff
- Welcome to the C-Level (with Nate Warfield)
- Wisdom from the 1st Cyber Colonel (JC Vega)
Defensive Technologies is about creating defense in depth in an organization to protect against a multitude of attacks. Knowledge of these domains is key as it’s one of the most common things auditors assess in an organization since it’s required for things like PCI compliance.
- Active Directory is Active with Attacks
- Allowlisting and Ringfencing (with Kieran Human)
- Attack Surface Management (with Richard Ford)
- Consolidating Vulnerability Management (with Jeff Gouge)
- Cryptography
- Data Protection (with Amer Deeba)
- Fun and Games to Stop Bad Actors (with Dr. Neal Krawetz)
- Got any Data Security (with Brian Vecci)
- Global War on Email
- I have more Agents than the FBI
- IPv6 Your Competitive Advantage (with Joe Klein)
- Mastering Defense Against Configurations ( Yuriy Tsibere)
- NSA's Top 10 Cybersecurity Mitigation Strategies
- One Vendor to Secure Them All
- Operational Resilience
- Outrunning the Bear
- SAST Security (with John Steven)
- Say Firewall One More Time
- Securing Small Businesses
- Stopping Attacks To Your Cloud Office Environment (with Rajan Kapoor)
- The Essential 8
- The Fab 5 Security Outcomes Study (with Helen Patton)
- Zero Trust isn't a product (with George Finney)
Detection & Response Capabilities is about creating an organization to identify how attackers might circumvent your organization’s defensive technologies. Since 100% protection isn’t achievable, it’s about effective incident response to cyber incidents such as ransomware or business email compromise. This section also includes Offensive Security Concepts, Business Continuity, and Disaster Recovery Planning.
- 10 Steps to Cyber Incident Response Playbooks
- Be SOCcessful with the SOC-CMM
- Brace for Incident (with Bryan Murphy)
- Breach and Attack Simulation (with Dave Klein)
- Building a Data Security Lake (with Noam Brosh)
- Build a World Class SOC (with Carson Zimmerman)
- Cyber Deception (with Kevin Fiscus)
- Cyber Ranges (with Debbie Gordon)
- Cyber Threat Intelligence (with Jeff Majka & Andrew Dutton)
- Data Engineering (with Gal Shpantzer)
- Deceive to Detect (with Yuriy Gatupov)
- Everything you wanted to know about Ransomware
- Flirting with Disaster
- From Hunt Team to Hunter (with Bryce Kunz)
- Got any Threat Intelligence? (with Landon Winkelvoss)
- How to Stop Bad Guys from Staying on Your Network (with Kevin Fiscus)
- Inside the 2024 Verizon Data Breach Investigations Report
- Inside the 2025 Verizon Data Breach Investigations Report
- Insider Threat (with Shawnee Delaney)
- Insider Threat Operations (with Jim Lawler)
- Logging in with SIEMs (with Anton Chuvakin)
- Modernizing our SOC Ingest (with JP Bourget)
- Ransomware Response (with Ricoh Danielson)
- Salt Typhoon and Vulnerable Telecoms
- Shaping the SOC of Tomorrow (with Debbie Gordon)
- Slay the Dragon or Save the Princess?
- SMB CISO Challenges (with Kevin O'Connor)
- SOC Skills Part 1 (with Hasan Eksi)
- SOC Skills Part 2 (with Hasan Eksi)
- The Evolution of Data Loss Prevention (DLP)
- Transforming Security Operations (with Brian Carbaugh and William Macmillan)
Enabling Technologies is about enabling businesses to create digital transformation. This is helpful when organizations feel their technology is dated and want to adopt newer emerging technologies such as Artifical Intelligence, 5G, Internet of Things, Serverless Computing, Biometrics, Augmented/Virtual Reality, Blockchain, Robotics, Natural Language Processing, Quantum Computing, etc. Essentially this type of CISO focuses on technology transformation to enable the business.
- A CISO Primer on Agentic AI
- AI Coaching (with Tom Bendien)
- AI and ML and How to Tell When Vendors Are Full of It
- AI Just Changed Data Security Requirements (with Ronan Murphy)
- AI Mastery for CISOs: What You Must Know
- Avoiding Hurricanes in the Cloud
- Blockchain for CISOs
- Border Gateway Protocol (BGP)
- ChatGPT & Generative AI (with Konstantinos Sgantzos)
- CISO Predictions for 2023
- CISO Predictions for 2024
- CISO Predictions for 2025
- Cloud Drift (with Yoni Leitersdorf)
- Executive Updates to AI
- How AI Changes Talent Management (with Colleen Lennox)
- How to Compare Software
- How To Make Your AI Less Chatty (with Sounil Yu)
- How to Secure Generative AI
- Introduction to Docker Containers and Kubernetes (K8s)
- Introduction to the Cloud
- Microsoft Majorana is Taking the Quantum Leap
- Mobile Application Security (with Brian Reed)
- Model Context Protocol (MCP)
- Navigating the Cloud Security Landscape (with Chris Rothe)
- Repeatable, Attestable, and Defensible AI (with AWS's Former Deputy CISO Merritt Baer)
- SaaS Security Posture Management (with Ben Johnson)
- Securing the Cloud
- Unveiling AI and Crypto Threats with Microsoft's Tomas Roccia
- Web 3.0 Explained (with Aaron Markell)
- What most leaders don't understand about AI (with Dave Lewis)
Governance is about understanding what technology your organization uses so you can effectively manage it through a process. This can be particularly helpful when you need a CISO who can optimize how your resources are spent.
- A European View of CISO Responsibilities (with Michael Krausz)
- AI, Privacy, & Security Insights (with Aimee Cardwell)
- Asset Management
- Board Perspectives
- CIS CSAT (with Scott Gicking)
- Cyber Frameworks
- Cyber Defense Matrix (with Sounil Yu)
- Cyber Defense Matrix Reloaded (with Sounil Yu)
- Cyber Acronyms You Should Know
- Ethics and Artificial Intelligence (AI)
- Good Governance (with Sameer Sait)
- Measuring Results
- Methodologies for Analysis (with Christopher Crowley)
- IT Governance
- Shadows and Zombies in the Data Center
- Simple, Easy, & Cheap Cybersecurity Measures (with Brent Deterding)
- The 9 Cs of Cyber
- The Cost of Cyber Defense
- The OWASP Threat and Safeguard Matrix (with Ross Young)
- The Full Irish
Identity & Access Management is about limiting the scope of an attacker who could cause harm to your organization. This is a key skill set for organizations that use lots of technologies from external vendors/providers. This knowledge is also helpful for organizations where data sharing agreements with partners and third parties is common.
- Authentication, Rainbow Tables, and Password Managers
- Betting on MFA
- Identity and Access Management is the New Perimeter
- Knock Knock, Who's There and Whatcha Want?
- MFA Mishaps
- Pass the Passwords
- The IAM Masterclass
- Zero Trust
Laws, Regulations, and Oversight is about ensuring compliance with appropriate laws and regulations. This is particularly useful in highly regulated industries (Financial Services or Medical Industry). Organizations that are coming out of a data breach scenario are also likely to find increased scrutiny by regulators/auditors.
- Brace for Audit (with Brian Murphy)
- Build a World Class GRC Program (with Matt Hillary)
- Copywriting AI (with Mark Rasch)
- Cyber Law Musings (with Mark Rasch)
- Cyber Security Laws and Regulations
- Cyberwar and the Law of Armed Conflict (with Lary Dietz)
- CMMC and Me
- Emerging Risks with the Chertoff Group
- Ethics (with Stephen Northcutt)
- Executive Order on Improving the Nation’s Cybersecurity
- Fedshark's Blueprint for Cost Effective Risk Reduction
- From Breach to Bench (with Thomas Ritter)
- Handling Regulatory Change
- Legal Questions (with Evan Wolff)
- Lawyers, Breaches, and CISOs: Oh My (with Thomas Ritter)
- Living in a Materiality World
- Navigating NYDFS Cyber Regulation
- Tim Brown on SolarWinds: What Every CISO Should Know
Product Security is focused on ensuring developers write secure code. This can be a competitive advantage for organizations that build large amounts of custom code.
- A CISO's Guide to Pentesting
- Complexity is Killing Us
- DARPA’s AI Cyber Challenge Unveiled (with Andrew Carney)
- DevOps
- Easier, Better, Faster, & Cheaper Software
- The Three Ways of DevOps
- Mastering Vulnerability Management
- Modern Software Development Practices
- OWASP Top 10 Web Application Attacks
- Navigating Software Supply Chain Security (with Cassie Crossley)
- Patch or Perish (with Ross Young)
- Pentesting for Readiness Not Compliance (with Snehal Antani)
- Setting Up an Application Security Program
- Tackle Your Technical Debt
- The TTPs of a Security Champions Program (with Dustin Lehr)
- Threat Modeling (with Adam Shostack)
- Understanding the Critical Role of CVEs and CVSS
- Understanding Vulnerabilities, Exploits, and Cybersecurity (with Patrick Garrity and Tod Beardsley)
- Vibe Coding Security (with Neatsun Ziv)
- Vulnerability Management (with Chris Hughes)
- Working on the Supply Chain Gang
Risk Management is about effectively identifying what the biggest risks to the company are, what's the likelihood and magnitude of an attack, and how much does it cost to remediate. This is helpful for organizations who want more transparency.
- Cybersecurity First Principles (with Rick Howard)
- Cyber War
- Includes No Dirt (with Bill Dougherty)
- Risky Business
- More Risky Business with FAIR
- Protecting your Crown Jewels (with Roselle Safran)
- Table Top Exercises
- The Impact of the Israel Iran Conflict (with Nathan Case)
- Third Party Risk Management (with Scott Fairbrother)
- Why CISOs Miss the Next Big Security Challenge (with Richard Stiennon)
Security Culture is about building an organization where the entire company becomes resilient. Building culture requires a strong focus on promoting security awareness and training so employees don’t click malicious links or send sensitive data outside the company.
- 40 Years of Career Advice in 40 Minutes
- Actionable Gamification and Lasting Success (with Yu-Kai Chou)
- AI Singularity (with Richard Thieme)
- Aligning Security Initiatives with Business Objectives
- Avoiding Death by PowerPoint
- Behavioral Insights (with Dr. Dustin Sachs)
- Bobby the Intern
- Breaking Backbones (with Deb Radcliff)
- Busy is the New Stupid (with Ross Young)
- Change Management
- Countering Corporate Espionage
- Cyber Thrills and Auther Quills with (Deb Radcliff)
- Cybersecurity Apprenticeships (with Craig Barber)
- Cybersecurity Crisis: Are We Failing the Next Generation?
- From CruiseCon to AI Threats (with Ira Winkler)
- From Cyber Burnout to VCISO Bliss (with Olivia Rose)
- From Invention to Entrepreneurship (with Jeri Ellsworth)
- Game-Based Learning (with Andy Serwin & Eric Basu)
- Hacker Summer Camp
- How to Become a Cyber Security Expert
- How to Build a Successful Cybersecurity Startup (with Ross Haleliuk)
- Ira Winkler CruiseCon Founder
- Listening to the Wise (with Bill Cheswick)
- Metrics that Matter
- Mentorship, Sponsorship, and A Message to Garcia
- Navigating Hacker Summer Camp 2025
- Powerful Questions
- Roses, Buds, & Thorns
- Secure Developer Training Programs (with Scott Russo) Part 1
- Secure Developer Training Programs (with Scott Russo) Part 2
- Securing the Business Processes
- Security Team Operating System (with Christian Hyatt)
- Shall We Play A Game?
- Start Me Up (with Bob Cousins)
- Tackling 3 Really Hard Problems in Cyber (with Andy Ellis)
- The 7 Broken Pillars of Cybersecurity
- The 7 Lies in Cyber
- The Business Case for a Global Lead of Field Cybersecurity (with Joye Purser)
- There's Room For Everybody In Your Router (with Giorgio Perticone)
- Thought Provoking Discussions (with Richard Thieme)
- Wonderful Winn Schwartau
Helpful Topics to improve the quality of life for Cyber Executives
- Breaking into Cybersecurity (with Christophe Foulon)
- CISO Burnout (with Raghav Singh)
- Financial Planning (with Logan Jackson)
- From Hacking to Hardcover (with Bill Pollock)
- Founding to Funding (with Cyndi and Ron Gula)
- Mastering Cybersecurity Recruitment and Career Growth (with Casey Marquette)
- Protecting Your Family
- Stressed Out? Find your Ikigai and 6 Invaluable Factors
- The Secret to Career Success: Your Personal Board of Directors
- The Seesaw of Cyber Recruiting (with Lee Kushner)

