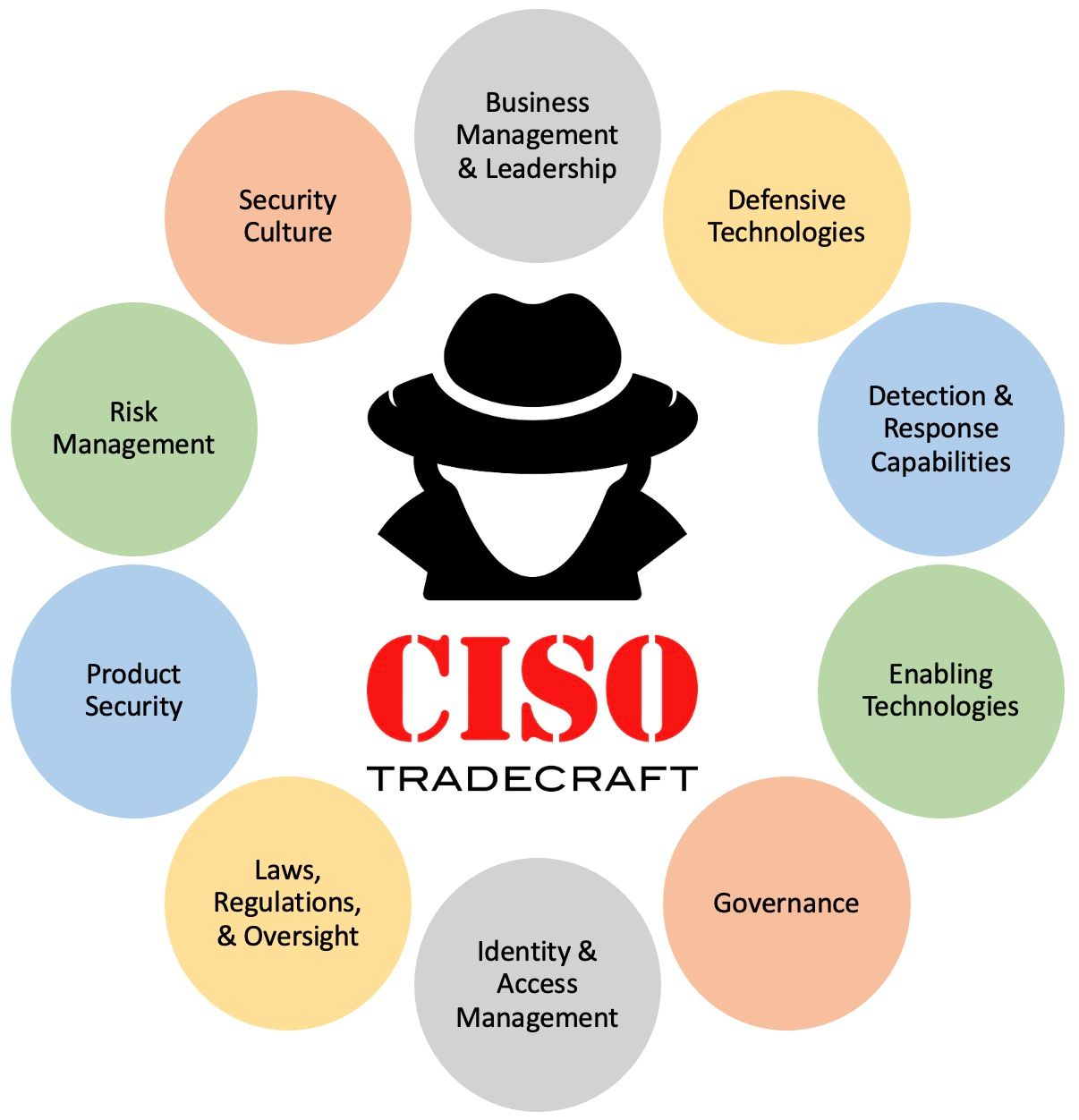
CISO Role
This topic is used to increase understanding about the position of a Chief Information Security Officer (CISO). It also provides tips to help cyber executives succeed such as Building a Cyber Strategy.
- What is a CISO
- 3 Business Objectives & 5 CISO Archetypes
- 7 Ways CISOs Setup for Success
- Board Decks (with Demetrios Lazarikos)
- Career Lessons from a CISO
- CISO Knowledge Domains Part 1
- CISO Knowledge Domains Part 2
- How do CISOs spend their time?
- How to Win Your First CISO Role
- Lessons Learned as a CISO
- Negotiating Your Best CISO Package
- Refreshing Your Cybersecurity Strategy
- The CISO Mindmap (with Rafeeq Rehman)
- 2024 CISO Mindmap (with Rafeeq Rehman)
- The 3 Keys to being a CISO
- The 30 Year CISO Evolution
- The Professionalization of CISOs
- Updating the Executive Leadership Team
- Updating the Mindmap
- Your First 90 Days as a CISO
Business Management & Leadership
Essential soft skills for executives to lead, influence, and implement change via large collaboration efforts.
- 1% Better Leadership
- Black Hat Chat with ThreatLocker CEO
- Accepted Cyber Security Strategy
- Addressing the Top CEO Concerns
- Connecting the Dots
- Crisis Leadership (9/11 Experience)
- Crucial Conversations
- Effective Meetings
- Emotional Intelligence
- Ensuring Profitable Growth
- Executive Competencies
- Executive Presence
- Framing Executive Discussions
- Gaining Trust (with Robin Dreeke)
- Grey is the New Black
- How to Read Your Boss
- Leading with Style
- Master Storytelling for CISOs
- Maximize Outcomes Per Dollar
- Maximize Cybersecurity Budgets
- New Kid in Town
- Partnership is Key
- Presentation Skills
- Principles of Persuasion
- Promotion through Politics
- Reality-Based Leadership
- Responsibility, Accountability, Authority
- Show Me the Money
- Speak My Language
- Team Building
- Demise of the Cyber Workforce
- The Great Resignation
- The Right Stuff
- Welcome to the C-Level
- Wisdom from the 1st Cyber Colonel
Defensive Technologies
Creating defense in depth to protect against attacks. Knowledge here is key for auditing and compliance (e.g., PCI).
- Active Directory is Active with Attacks
- Allowlisting and Ringfencing
- Attack Surface Management
- Consolidating Vulnerability Management
- Cryptography
- Data Protection
- Fun and Games to Stop Bad Actors
- Got any Data Security?
- Global War on Email
- I have more Agents than the FBI
- IPv6 Your Competitive Advantage
- Mastering Defense Against Configurations
- NSA's Top 10 Mitigation Strategies
- One Vendor to Secure Them All
- Operational Resilience
- Outrunning the Bear
- SAST Security
- Say Firewall One More Time
- Securing Small Businesses
- Stopping Attacks To Cloud Office
- The Essential 8
- The Fab 5 Security Outcomes Study
Detection & Response Capabilities
Identifying how attackers circumvent defenses and effective incident response. Includes Offensive Security, Business Continuity, and DR.
- 10 Steps to Incident Response Playbooks
- Be SOCcessful with the SOC-CMM
- Brace for Incident
- Breach and Attack Simulation
- Building a Data Security Lake
- Build a World Class SOC
- Cyber Deception
- Cyber Ranges
- Cyber Threat Intelligence
- Data Engineering
- Deceive to Detect
- Everything about Ransomware
- Flirting with Disaster
- From Hunt Team to Hunter
- Got any Threat Intelligence?
- Stopping Bad Guys on Your Network
- Inside the 2024 Verizon DBIR
- Inside the 2025 Verizon DBIR
- Insider Threat
- Insider Threat Operations
- Logging in with SIEMs
- Modernizing our SOC Ingest
- Ransomware Response
- Salt Typhoon and Vulnerable Telecoms
- Shaping the SOC of Tomorrow
- Slay the Dragon or Save the Princess?
- SMB CISO Challenges
- SOC Skills Part 1
- SOC Skills Part 2
- Evolution of Data Loss Prevention (DLP)
- Transforming Security Operations
Enabling Technologies
Using emerging technologies (AI, 5G, IoT, Blockchain, Quantum) to enable digital transformation and business growth.
- A CISO Primer on Agentic AI
- AI Coaching
- AI/ML: When Vendors Are Full of It
- AI Just Changed Data Security Requirements
- AI Mastery for CISOs
- Avoiding Hurricanes in the Cloud
- Blockchain for CISOs
- Border Gateway Protocol (BGP)
- ChatGPT & Generative AI
- CISO Predictions for 2023
- CISO Predictions for 2024
- CISO Predictions for 2025
- Cloud Drift
- Executive Updates to AI
- How AI Changes Talent Management
- How to Compare Software
- How To Make Your AI Less Chatty
- How to Secure Generative AI
- Intro to Docker & Kubernetes (K8s)
- Introduction to the Cloud
- Microsoft Majorana & Quantum Leap
- Mobile Application Security
- Model Context Protocol (MCP)
- Navigating Cloud Security Landscape
- Repeatable, Attestable, Defensible AI
- SaaS Security Posture Management
- Securing the Cloud
- Unveiling AI and Crypto Threats
- Web 3.0 Explained
- What leaders don't understand about AI
Governance
Understanding your technology and managing it through process and optimization.
- A European View of CISO Responsibilities
- AI, Privacy, & Security Insights
- Asset Management
- Board Perspectives
- CIS CSAT (with Scott Gicking)
- Cyber Frameworks
- Cyber Defense Matrix
- Cyber Defense Matrix Reloaded
- Cyber Acronyms You Should Know
- Ethics and Artificial Intelligence (AI)
- Good Governance (with Sameer Sait)
- Measuring Results
- Methodologies for Analysis
- IT Governance
- Shadows and Zombies in the Data Center
- Simple, Easy, & Cheap Cybersecurity Measures
- The 9 Cs of Cyber
- The Cost of Cyber Defense
- The OWASP Threat and Safeguard Matrix
- The Full Irish
Identity & Access Management
Limiting the scope of attackers and managing access for vendors and third parties.
- Authentication, Rainbow Tables, & Password Managers
- Betting on MFA
- Identity and Access Management is the New Perimeter
- Knock Knock, Who's There and Whatcha Want?
- MFA Mishaps
- Pass the Passwords
- The IAM Masterclass
- Zero Trust
Laws, Regulations, & Oversight
Compliance with laws and regulations, particularly for highly regulated industries like Finance and Medical.
- Brace for Audit
- Build a World Class GRC Program
- Copywriting AI (with Mark Rasch)
- Cyber Law Musings (with Mark Rasch)
- Cyber Security Laws and Regulations
- Cyberwar and the Law of Armed Conflict
- CMMC and Me
- Emerging Risks with the Chertoff Group
- Ethics (with Stephen Northcutt)
- Executive Order on Improving Cybersecurity
- Fedshark's Blueprint for Risk Reduction
- From Breach to Bench
- Handling Regulatory Change
- Legal Questions (with Evan Wolff)
- Lawyers, Breaches, and CISOs: Oh My
- Living in a Materiality World
- Navigating NYDFS Cyber Regulation
- Tim Brown on SolarWinds: What Every CISO Should Know
Product Security
Ensuring developers write secure code. A competitive advantage for organizations with custom software.
- A CISO's Guide to Pentesting
- Complexity is Killing Us
- DARPA’s AI Cyber Challenge Unveiled
- DevOps
- Easier, Better, Faster, & Cheaper Software
- The Three Ways of DevOps
- Mastering Vulnerability Management
- Modern Software Development Practices
- OWASP Top 10 Web Application Attacks
- Navigating Software Supply Chain Security
- Patch or Perish (with Ross Young)
- Pentesting for Readiness Not Compliance
- Setting Up an Application Security Program
- Tackle Your Technical Debt
- The TTPs of a Security Champions Program
- Threat Modeling (with Adam Shostack)
- Understanding CVEs and CVSS
- Understanding Vulnerabilities, Exploits, & Cybersecurity
- Vibe Coding Security
- Vulnerability Management (with Chris Hughes)
- Working on the Supply Chain Gang
Risk Management
Identifying risks, likelihood, magnitude, and remediation costs to ensure transparency.
- Cybersecurity First Principles
- Cyber War
- Includes No Dirt (with Bill Dougherty)
- Risky Business
- More Risky Business with FAIR
- Protecting your Crown Jewels
- Table Top Exercises
- The Impact of the Israel Iran Conflict
- Third Party Risk Management
Security Culture
Building a resilient organization through security awareness and training.
- 40 Years of Career Advice in 40 Minutes
- Actionable Gamification and Lasting Success
- AI Singularity
- Aligning Security Initiatives with Business Objectives
- Avoiding Death by PowerPoint
- Breaking Backbones (with Deb Radcliff)
- Bobby the Intern
- Change Management
- Countering Corporate Espionage
- Cyber Thrills and Auther Quills
- Cybersecurity Apprenticeships
- Cybersecurity Crisis: Failing the Next Generation?
- From CruiseCon to AI Threats
- From Cyber Burnout to VCISO Bliss
- From Invention to Entrepreneurship
- Game-Based Learning
- Hacker Summer Camp
- How to Become a Cyber Security Expert
- How to Build a Successful Cybersecurity Startup
- Ira Winkler CruiseCon Founder
- Listening to the Wise (with Bill Cheswick)
- Metrics that Matter
- Mentorship, Sponsorship, and A Message to Garcia
- Navigating Hacker Summer Camp 2025
- Powerful Questions
- Roses, Buds, & Thorns
- Secure Developer Training Programs Part 1
- Secure Developer Training Programs Part 2
- Securing the Business Processes
- Security Team Operating System
- Shall We Play A Game?
- Start Me Up (with Bob Cousins)
- Tackling 3 Really Hard Problems in Cyber
- The 7 Broken Pillars of Cybersecurity
- The 7 Lies in Cyber
- Business Case for Global Lead of Field Cyber
- There's Room For Everybody In Your Router
- Thought Provoking Discussions
- Wonderful Winn Schwartau
Other Topics
Helpful Topics to improve the quality of life for Cyber Executives
- Breaking into Cybersecurity
- CISO Burnout
- Financial Planning
- From Hacking to Hardcover
- Founding to Funding
- Mastering Cybersecurity Recruitment
- Protecting Your Family
- Stressed Out? Find your Ikigai
- Secret to Career Success: Personal Board
- The Seesaw of Cyber Recruiting